What Is DNS Spoofing?
DNS Spoofing (sometimes referred to as DNS Cache Poisoning) is an attack whereby a host with no authority is directing a Domain Name Server (DNS) and all of its requests. This basically means that an attacker could redirect all DNS requests, and thus all traffic, to his (or her) machine, manipulating it in a malicious way and possibly stealing data that passes across. This is one of the more dangerous attacks as it is very difficult to detect, but today I will show you both how to perform it and how to detect if it is being performed by somebody else on your network.
Step 1: Preparation Let's start by booting up Kali Linux, whether it's a Virtual Machine (VM), a native boot, or a dual boot. If you haven't got Kali yet (which you should by now, granted that you're on this website) go get it on the official website.Make sure you have a working internet connection before you continue and make sure that you are on the same network as your target. This is a LAN (or WLAN) attack and so both the attacker and victim must have the same network gateway. Let me point out in advance that the victim could be running any operating system, it does not matter.
Step 2: Configuring We now need to edit the Ettercap configuration file since it is our application of choice for today. Let's navigate to /etc/ettercap/etter.conf and open the file with a text editor like gedit and edit the file. We can use Terminal for that.
COMMAND => gedit /etc/ettercap/etter.conf
Now scroll down until you find the heading that says Linux and under that
remove both the # signs below where it says “if you use iptables”.
DNS Spoofing (sometimes referred to as DNS Cache Poisoning) is an attack whereby a host with no authority is directing a Domain Name Server (DNS) and all of its requests. This basically means that an attacker could redirect all DNS requests, and thus all traffic, to his (or her) machine, manipulating it in a malicious way and possibly stealing data that passes across. This is one of the more dangerous attacks as it is very difficult to detect, but today I will show you both how to perform it and how to detect if it is being performed by somebody else on your network.
Step 1: Preparation Let's start by booting up Kali Linux, whether it's a Virtual Machine (VM), a native boot, or a dual boot. If you haven't got Kali yet (which you should by now, granted that you're on this website) go get it on the official website.Make sure you have a working internet connection before you continue and make sure that you are on the same network as your target. This is a LAN (or WLAN) attack and so both the attacker and victim must have the same network gateway. Let me point out in advance that the victim could be running any operating system, it does not matter.
Step 2: Configuring We now need to edit the Ettercap configuration file since it is our application of choice for today. Let's navigate to /etc/ettercap/etter.conf and open the file with a text editor like gedit and edit the file. We can use Terminal for that.
COMMAND => gedit /etc/ettercap/etter.conf
Step 3: Ettercap
Now let's run this show by opening Ettercap. You can do it the lame way
through launchpad or the cool way using Terminal. I'm going to teach you
the cool way. Go ahead and open up Terminal and type:
COMMAND => ettercap -G
First select Sniff > Unified sniffing… > (Select the interface connected to the internet) > OK
(You can find out which interface is connected to the internet by typing in Terminal ifconfig and seeing which interface gives you an IP address).
Then swiftly do Start > Stop sniffing because it automatically starts sniffing after we press OK and we don't want that.
Now we want to scan for targets on our network and pick one. To do this, go to Hosts > Scan for hosts and wait until it does the scan. It should only take a few seconds depending on the size of your network (which I assume isn't very large).
So we've dealt with the scanning but how do we see our targets? Well, go
back to Hosts and select Host list to see all the targets that Ettercap has
found.
Now what we want to do is add our victim machine to Target 1 and our network gateway to Target 2 but first we need to know both of their IP addresses. To find out our victim's IP address, we first need to know who we are attacking, and we can do so using nmap to find the information we need on the target machine. Once you are sure who your victim is, select their IP address from the host list in Ettercap and choose Add to Target 1. Now you need to find your gateway IP address (your router). To do this, open Terminal and type ifconfig and look at where it says Bcast: and that will tell you the IP address of your gateway. Now select that from the host list as well and choose Add to Target 2.
Now what we want to do is add our victim machine to Target 1 and our network gateway to Target 2 but first we need to know both of their IP addresses. To find out our victim's IP address, we first need to know who we are attacking, and we can do so using nmap to find the information we need on the target machine. Once you are sure who your victim is, select their IP address from the host list in Ettercap and choose Add to Target 1. Now you need to find your gateway IP address (your router). To do this, open Terminal and type ifconfig and look at where it says Bcast: and that will tell you the IP address of your gateway. Now select that from the host list as well and choose Add to Target 2.
Step 4: Action
Now that we have both Targets set to our victim and gateway, we can
proceed to the attack.
Go to the MITM tab and select ARP poisoning, choose Sniff remote
connections and press OK. Now go to Plugins > Manage the plugins and
double click dns_spoof to activate that plugin.
We now need to edit another file in the Ettercap folder
COMMAND => gedit /etc/ettercap/etter.dns
This etter.dns file is the hosts file and is responsible for redirecting specific DNS requests. Basically, if the target enters facebook.com they will be redirected to Facebook's website, but this file can change all of that. This is where the magic happens, so let's edit it. First, however, let me explain what can and should be done with the hosts file. So in a real life scenario, an attacker would use this opportunity to redirect traffic to their own machine for data sniffing. This is done by starting an Apache server on the Kali machine and changing the default homepage to a clone of, let's say facebook.com or chase.com so that when the victim visits those websites, after being redirected to the attacker machine they will see the clones of the aforementioned sites. This will probably fool the unsuspecting user into entering their credentials where they really shouldn't. Enough talk, let's do it.
First, redirect traffic from any website you would like to your Kali machine. For that, go down to where it says "microsoft sucks ;)" and add another line just like that below it, but now use whatever website you would like. Also, don't forget to change the IP address to your IP address.
Now we need to start Apache to accept incoming traffic.
COMMAND => service apache2 start
Let's head over to the default html page folder. That is where we can take control of what the victim sees when they get redirected. The location is /var/www/html where you will find the index.html page. You can alter the document to your needs and, once you think you have done sufficient fooling to your victim, you can save the page and changes will take effect instantly. Let's see here...
The final thing left to do here is to start the attack. Go back to Ettercap and
select Start > Start sniffing and that should do it.
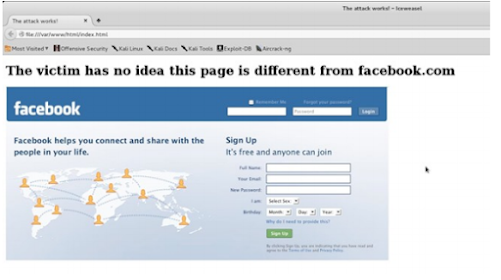
Now every time the victim visits the webpage you indicated in the etter.dns
file (in my case it's facebook.com) they will be redirected to the fancy and
inconspicuous page above. You can see how this can be extremely
malicious, since the attacker could write a script that fetches the requested
page immediately and sets up the etter.dns file and listens in on the login,
all automatically. This should really alert you that it is really that simple to
perform a DNS Spoofing attack with very few resources.
Detection : So how do you protect yourself from it? There are a couple of ways: using software built for ARP poisoning detection or checking the arp command manually on a regular basis (which is a pain). Let's look at the software first, there are a few that I will mention
To check the ARP cache, go to the Terminal and type arp -a and you will see several entries like this:
COMMAND => arp -a
If you can remember something like the first 6 characters of your gateway's MAC address and continually check arp -a to see if it matches, then you've got yourself a way to detect ARP poisoning without needing any 3rd party software.
THANK YOU😊😊
We now need to edit another file in the Ettercap folder
COMMAND => gedit /etc/ettercap/etter.dns
This etter.dns file is the hosts file and is responsible for redirecting specific DNS requests. Basically, if the target enters facebook.com they will be redirected to Facebook's website, but this file can change all of that. This is where the magic happens, so let's edit it. First, however, let me explain what can and should be done with the hosts file. So in a real life scenario, an attacker would use this opportunity to redirect traffic to their own machine for data sniffing. This is done by starting an Apache server on the Kali machine and changing the default homepage to a clone of, let's say facebook.com or chase.com so that when the victim visits those websites, after being redirected to the attacker machine they will see the clones of the aforementioned sites. This will probably fool the unsuspecting user into entering their credentials where they really shouldn't. Enough talk, let's do it.
First, redirect traffic from any website you would like to your Kali machine. For that, go down to where it says "microsoft sucks ;)" and add another line just like that below it, but now use whatever website you would like. Also, don't forget to change the IP address to your IP address.
COMMAND => service apache2 start
Let's head over to the default html page folder. That is where we can take control of what the victim sees when they get redirected. The location is /var/www/html where you will find the index.html page. You can alter the document to your needs and, once you think you have done sufficient fooling to your victim, you can save the page and changes will take effect instantly. Let's see here...
Detection : So how do you protect yourself from it? There are a couple of ways: using software built for ARP poisoning detection or checking the arp command manually on a regular basis (which is a pain). Let's look at the software first, there are a few that I will mention
To check the ARP cache, go to the Terminal and type arp -a and you will see several entries like this:
COMMAND => arp -a
If you can remember something like the first 6 characters of your gateway's MAC address and continually check arp -a to see if it matches, then you've got yourself a way to detect ARP poisoning without needing any 3rd party software.
THANK YOU😊😊





Comments
Post a Comment